57%
The percentage of data breaches that involve internal actors.
10K
The number of enterprises that are making digital transformation happen. Want to know how?
70%
The percentage of IT decision makers that say technical debt has increased in the last year.
What can we help you with today?

adabas & natural
Enterprise Applications
Get more out of your enterprise systems. Develop, modernize and deploy your mission-critical applications on IBM Z® Systems, Linux® or cloud while connecting seamlessly to the latest innovations.

connx
Data Virtualization & Movement
Use CONNX to easily access, virtualize and move your data—wherever it is, however it’s structured—to power new apps, analytics, AI and hybrid cloud.

jopaz
Mainframe Optimization
Use JOPAZ to shift COBOL workloads off your central processor, immediately reduce MIPs, and free up capacity for innovation.
Want to try for yourself? Be our guest.
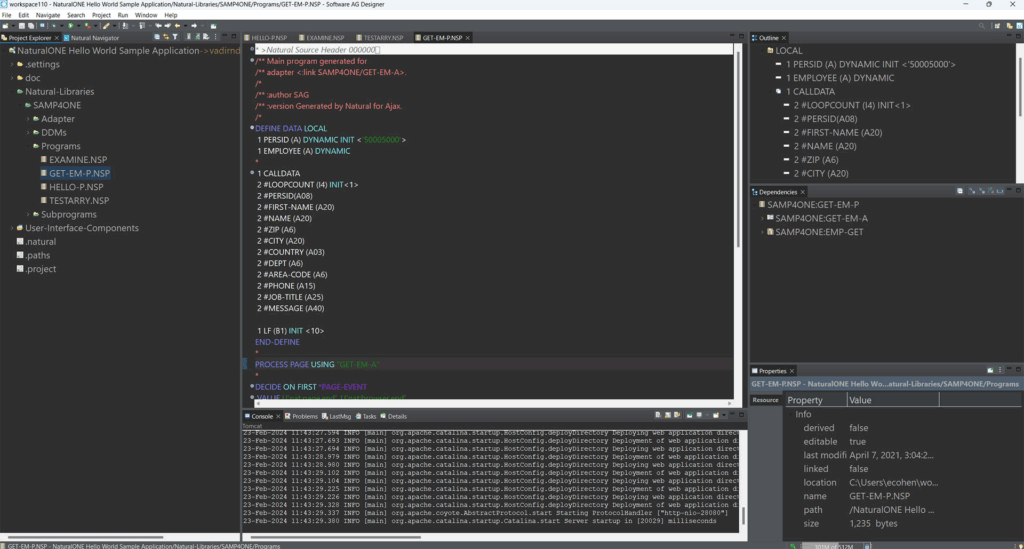
Build modern applications faster
- Develop high-performance applications in a modern DevOps environment
- Run on-prem, in the cloud or hybrid
- Connect seamlessly with new innovations
If our customers can do it, you can too.


DELJIS: Keeping Delaware safe with one criminal justice system
DELJIS has continuously modernized their IT—while relying on the rock-solid security and resiliency of its IBM Z platform to host decades of sensitive, highly regulated criminal justice data in Software AG’s Adabas database.
Just browsing? Here are some good reads.
Datasheet
Future-Proof Your Mission-Critical Apps with Adabas & Natural 2050+
Transform legacy applications while optimizing costs, modernizing development, and attracting new talent. Adabas & Natural 2050+ helps you balance innovation with efficiency.
whitepaper
Mainframe data integration for digital innovation and cloud analytics
Leverage your mainframe data to make better decisions and serve customers. The right approach to a hybrid architecture allows seamless operations between on-premises applications and cloud platforms.
webinar
Access, Analytics & AI: The 3 A’s of Mainframe Data Demands
Explore secure access, analytics, and AI for mainframe data. Learn scalable, no-code solutions that transform data management without sacrificing performance.
Datasheet
Adabas & Natural Managed Services
Overcome workforce challenges and optimize your Adabas & Natural environment with Software AG Managed Services.